Python SBOM and Supply Chain Vulnerability Reporting
Creating a software bill of materials and detecting vulnerabilities in Python dependency packages
Published on October 21, 2020 by Dai Tran
howto devsecops sbom supply-chain-security python dependency-vulnerabilities blog
2 min READ
The Context
The software bill of materials (SBOM) and supply chain (package dependency) security risks have been discussed a lot in the wake of the notorious Log4j vulnerability. My question was how to generate the SBOM, scan and report the dependency packages used by my Python code for vulnerabilities. Fortunately, I have found two tools that help me accomplish this:
The Action
Tool Installation
cyclonedx-bom
Install cyclonedx-bom from the Visual Studio Code Integrated Powershell terminal using pip:
pip install cyclonedx-bom
bomber
As bomber at the time of writing does not support Windows, I have to run a Debian based Docker container that have a volume mounted to the project root directory of my Python code, download the latest release and install it from there using the following command:
dpkg -i bomber_<version_number>_linux_arm64.deb
Tool Usage
SBOM Generation
In the Visual Studio Code Integrated Powershell terminal, run the following command to create the JSON SBOM file called pycyber.cyclonedxsbom.json in the sub directory sbom of the project root directory.
cyclonedx-py --format json -o ./sbom/pycyber.cyclonedxsbom.json -e
Dependency Package Vulnerability Scan
In the Debian based Docker container, cd into the sbom directory and run the following command to create a HTML dependency package vulnerability report there using the pycyber.cyclonedxsbom.json as the input.
root# cd sbom
root# bomber scan pycyber.cyclonedxsbom.json --output=html
The Result
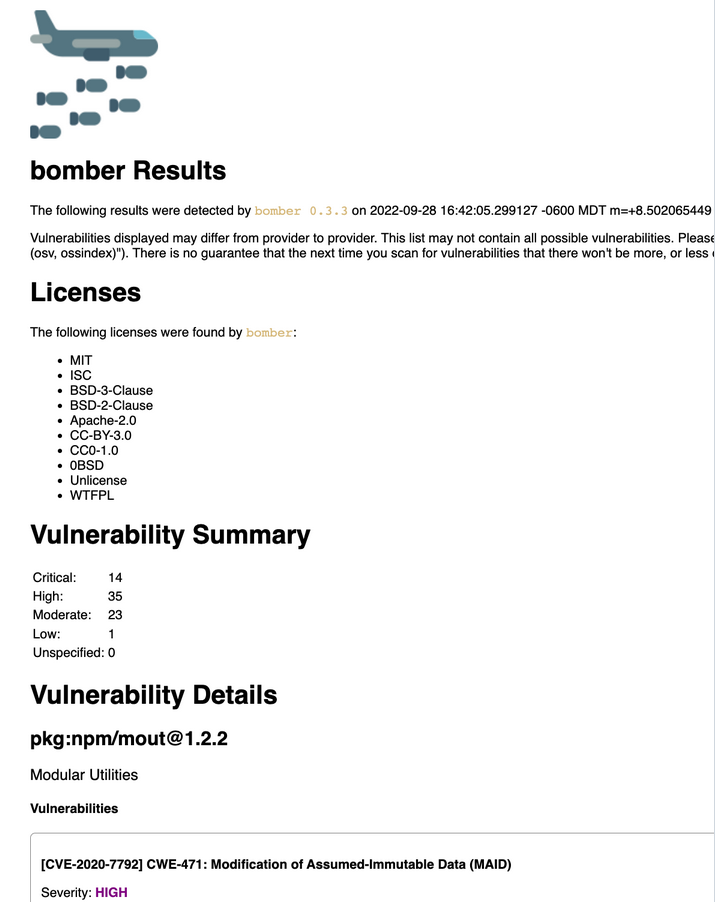
The report name follows this naming convention yyyymmdd-hh-mm-ss-bomber-results.html and looks like as follows.
Follow-Up Actions
The report show the vulnerable dependency packages and their versions. The pipdeptree tool can be used to identify the packages that require them using the following command.
pipdeptree -r -p MarkupSafe,numpy
I then update version numbers of the identified packages in the requirements.txt to the latest or the ones that do not use the vulnerable versions of the dependency packages. Finally, I regenerate SBOM and vulnerability report again to make sure that no vulnerabilities are reported.